Nessus Scans
Perform Nessus scans on OWASP BWA and DVWA, identify vulnerabilities and propose countermeasures.
Name: Anurodh Acharya
1. Perform a Basic Network Scan and Web Application Tests scan on both of the vulnerable machines. Make sure to record all scans using Wireshark.
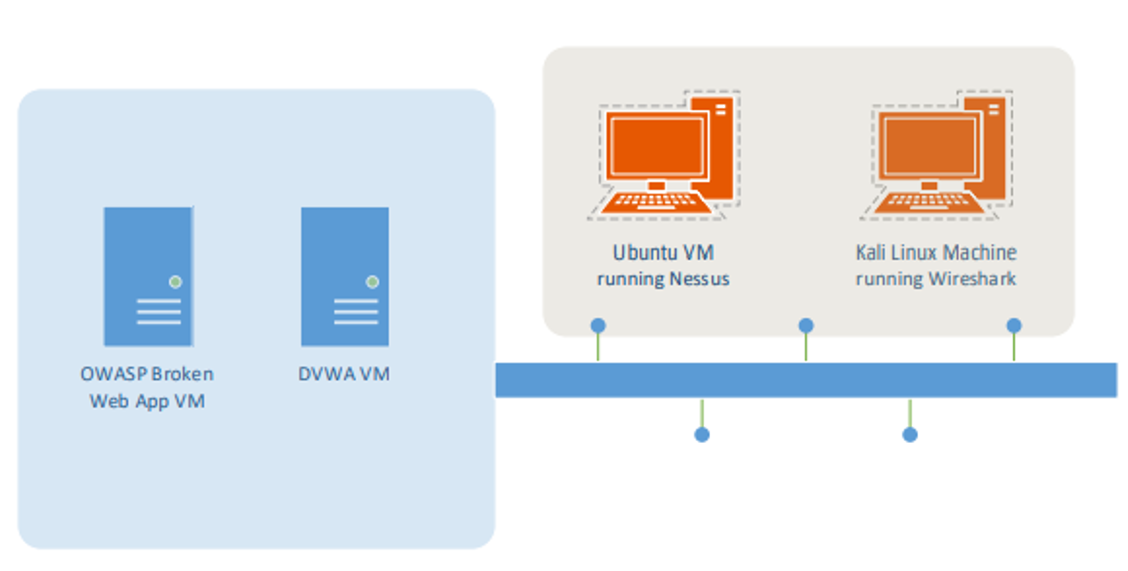
Network Configuration: Ubuntu
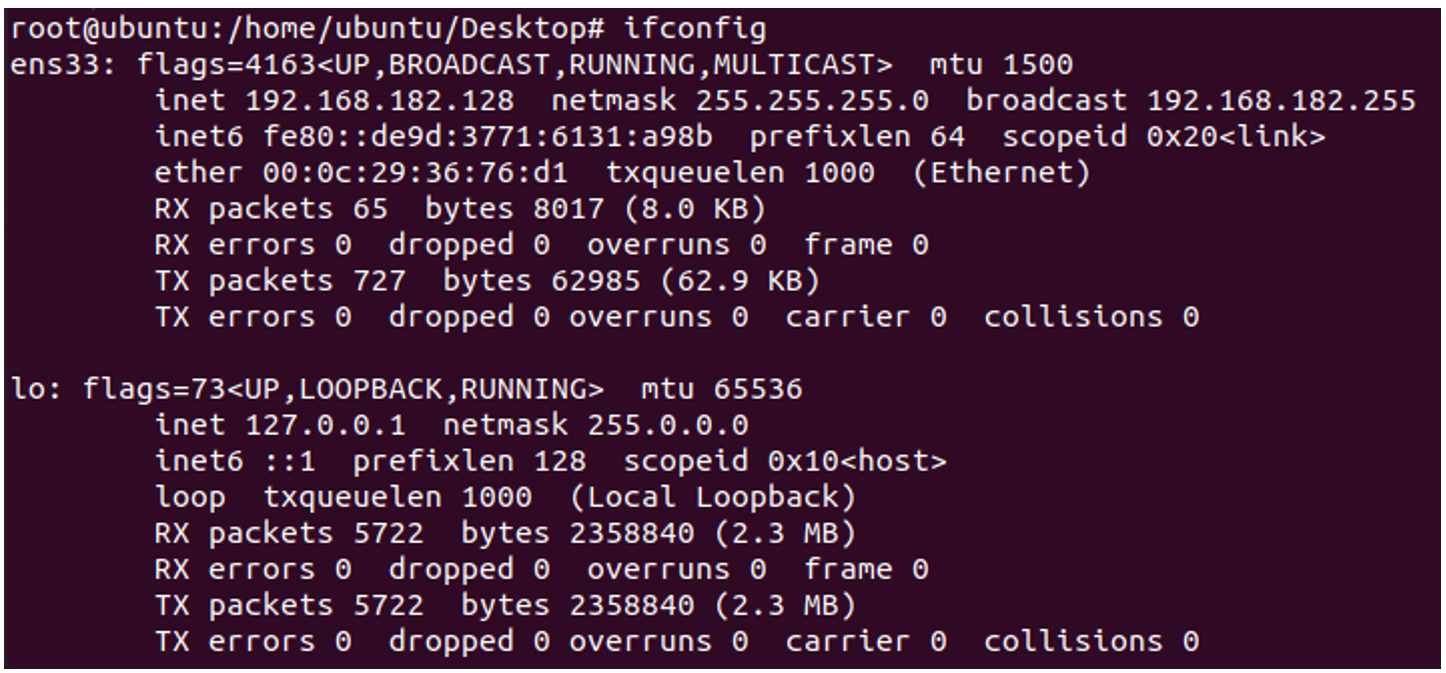
Network Configuration: OWASP BWA
Setting up Basic Network Scan on OWASP BWA
Basic Network Scan on OWASP BWA
Setting up the scan for Web Application Test on OWASP BWA
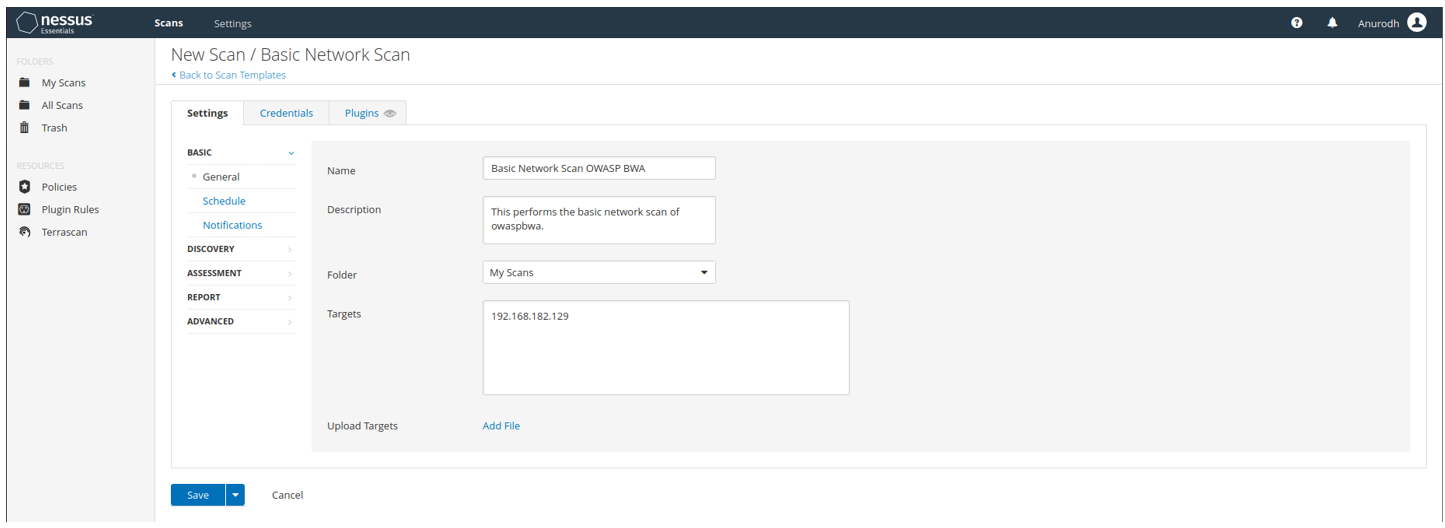
Web App Test Scan on OWASP BWA
Now it’s time to work with DVWA
Here, I will start capturing the packets.
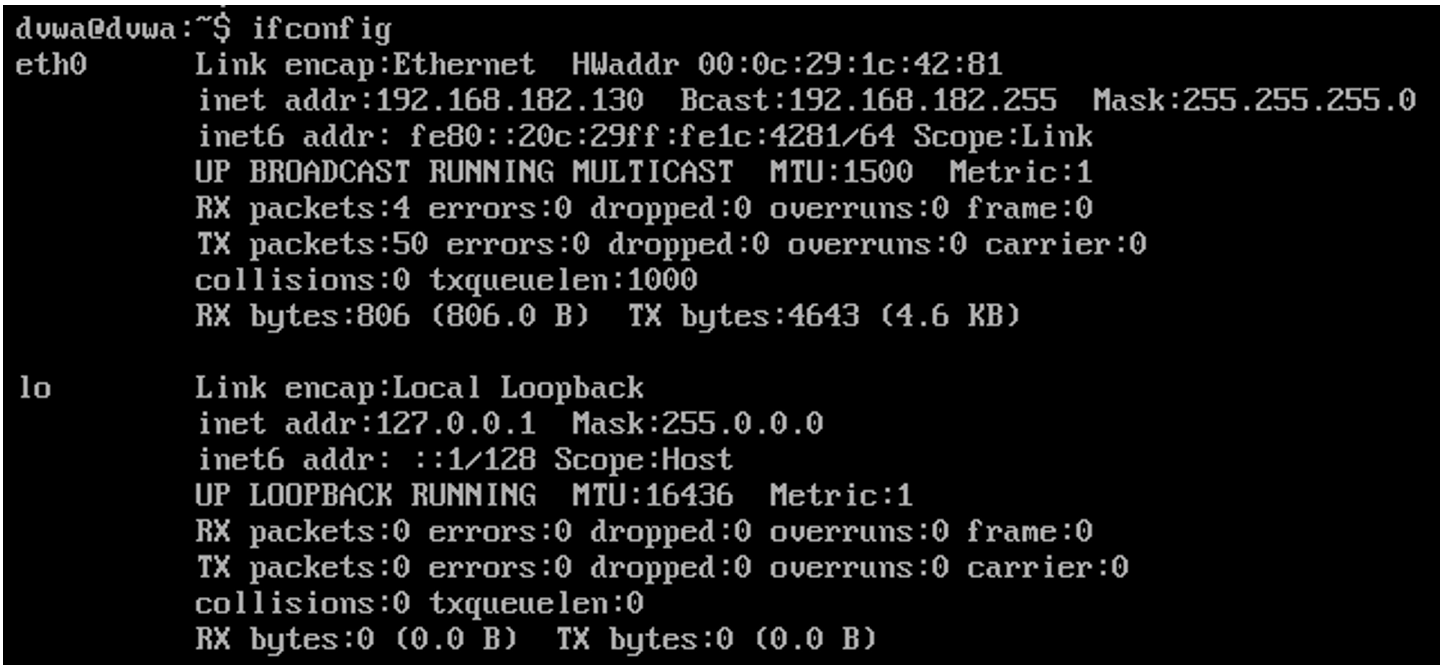
Ubuntu Network Scan Config on DVWA
Setting up the scan for Web Application Test on OWASP BWA.
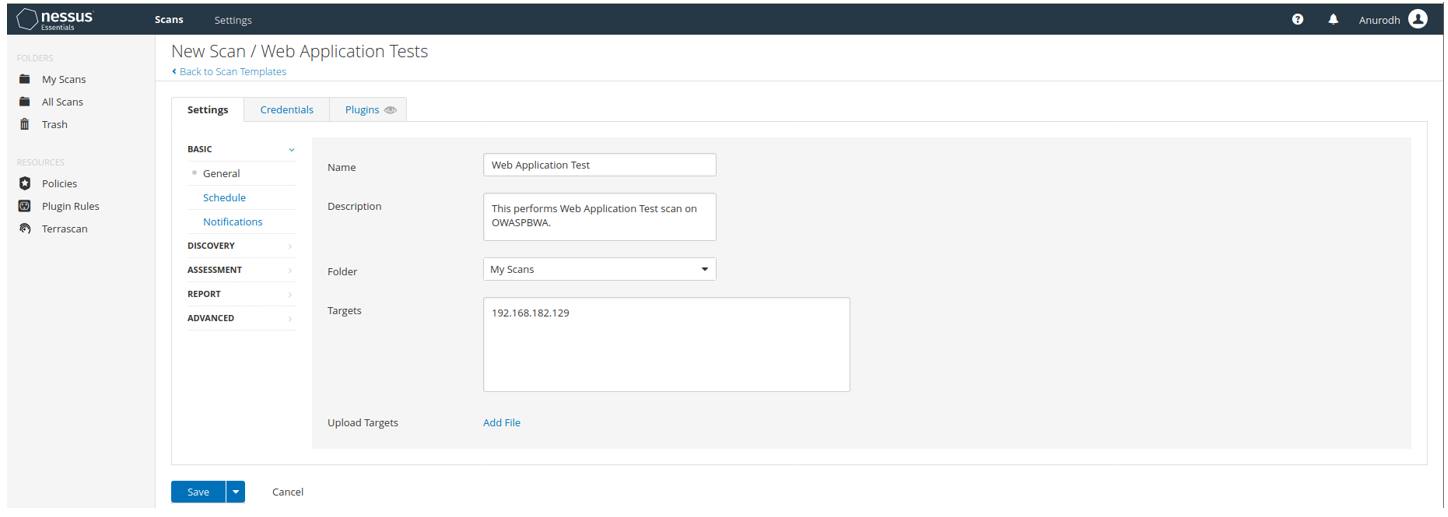
Now it’s time to work with DVWA.
Network Configuration: Ubuntu
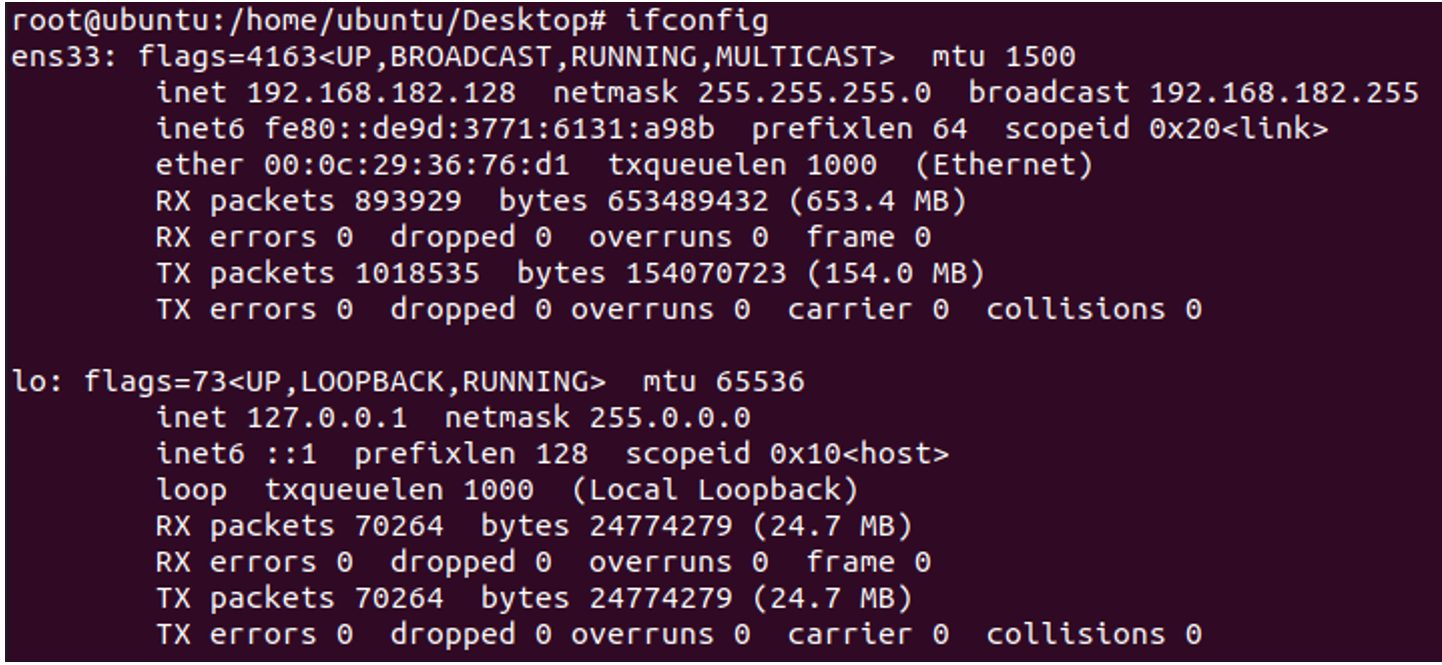
Network Configuration: DVWA
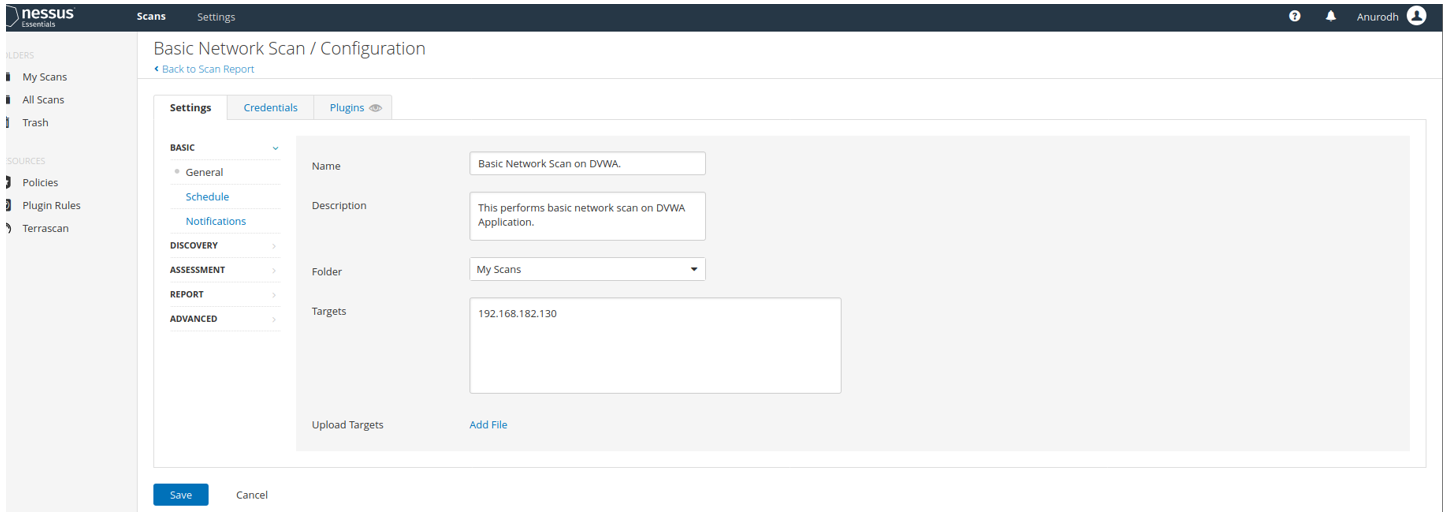
Below is the scan configuration for Basic Network Scan on DVWA.
SSLv2/v3 Detection on OWASP BWA
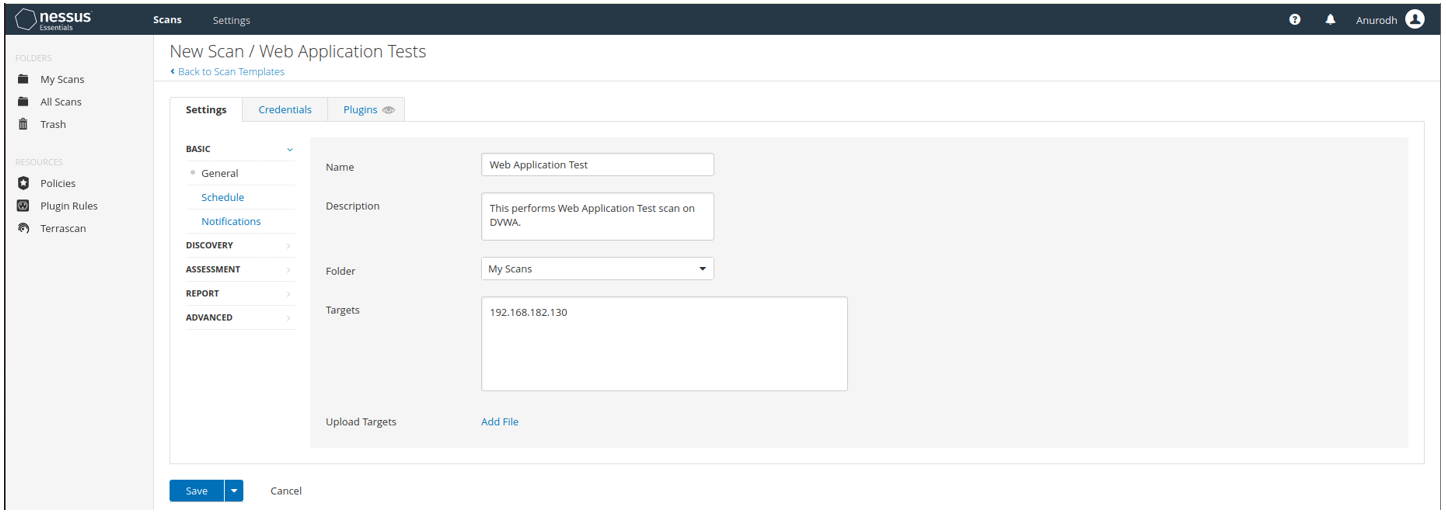
Below is the scan configuration for Web Application Test scan on DVWA.
Badlock Vulnerability on OWASP BWA
1. For each of the four scans, select a moderate or high risk vulnerability. Provide a description and suggest possible counter measure.
Problem
- The service is accepting encrypted connections using SSL version 2.0 or SSL version 3.0.
- These SSL versions have significant security cryptographic flaws.
- An attacker can perform cryptographic attacks and further do MITM attacks.
Solution
- It is suggested to disable both SSL version 2.0 and version 3.0.
- Make use of TLS version 1.2 and above.
Samba Badlock Vulnerability
Problem
- This is the vulnerability which exists in Security Account Manager (SAM) and Local Security Authority (LSAD).
- The attacker will be capable of reading and writing directly into the SAM database which will further allow the adversary to display all the passwords and other sensitive information that is present in the database.
Solution
- It is suggested to upgrade the samba version to 4.2.11, 4.3.8, 4.4.4 or later.
Web Application Test: SQLi Vulnerability
Problem
- The software running in remote host is vulnerable to SQL injection within the login forms.
- The adversary will be able to create a special crafted parameters to bypass the authentication mechanism.
Solution
- It is recommended to upgrade this to latest version of software which has appropriate input validations to stop this attack.
Web Application Test: XSS
Problem
- The JQuery version which has been used in the server is affected by multiple XSS vulnerabilities.
Solution
- It is recommended to upgrade the JQuery version to 3.5.0 or to a later one.
DVWA
Basic Network Scan: SSL Certificate Signed Using Weak Hashing Algorithm
Problem
- A weak hashing algorithm has been used by the service which are potentially vulnerable to collision attacks.
Solution
- Have the SSL reissued from the CA (Certificate Authority).
CVSS Score
- CVSS v3.0 Base Score: 7.5 (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N)
- CVSS v3.0 Temporal Score: 6.7 (CVSS:3.0/E:P/RL:O/RC:C)
- CVSS v2.0 Base Score: 5.0 (CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N)
- CVSS v2.0 Temporal Score: 3.9 (CVSS2#E:POC/RL:OF/RC:C)
OpenSSL < 0.9.8w ASN.1 asn1_d2i_read_bio Memory Corruption
Problem
- The web server is currently running a web server using OpenSSL version before 0.9.8w which is vulnerable to memory corruption vulnerability.
Solution
- It is suggested to upgrade the OpenSSL to 0.9.8w or later versions.
CVSS Score
- CVSS v2.0 Base Score: 7.5 (CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P)
- CVSS v2.0 Temporal Score: 5.9 (CVSS2#E:POC/RL:OF/RC:C)
Web Application Scan: phpMyAdmin Installation Not Password Protected
Problem
- The phpMyAdmin which has been installed on the web server provides unauthenticated access and does not require any identification.
- This will allow the adversaries to directly execute the SQL queries and process malicious codes remotely.
Solution
- Require an authentication mechanism to access phpMyAdmin.
Risk Factor
- High
CVSS v2.0 Base Score
- 7.5 (CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P)
Email Header Injection
Problem
- The current version of PHP which is running on the web servers is vulnerable to email header injection.
- This is due to not handling CR-LF sequences in the header fields.
Solution
- It is recommended to upgrade the PHP version to 7.3.28 or later one to mitigate this vulnerability.
Risk Factor
- Medium
CVSS v3.0 Base Score
- 5.3 (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N)
CVSS v2.0 Base Score
- 5.0 (CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N)
3. For the two Basic Network Scans, select a vulnerability that was detected on one of the machines but doesn’t show on the report of the other machine. Identify the Wireshark packets related to the detection/probing of this vulnerability on both scans.
Basic Network Scan
OWASP Broken Web Application: SMB Signing not required
Risk Factor
- Medium
CVSS v3.0 Base Score
- 5.3 (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N)
CVSS v3.0 Temporal Score - 4.6 (CVSS:3.0/E:U/RL:O/RC:C)
CVSS v2.0 Base Score - 5.0 (CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N)
CVSS v2.0 Temporal Score - 3.7 (CVSS2#E:U/RL:OF/RC:C)
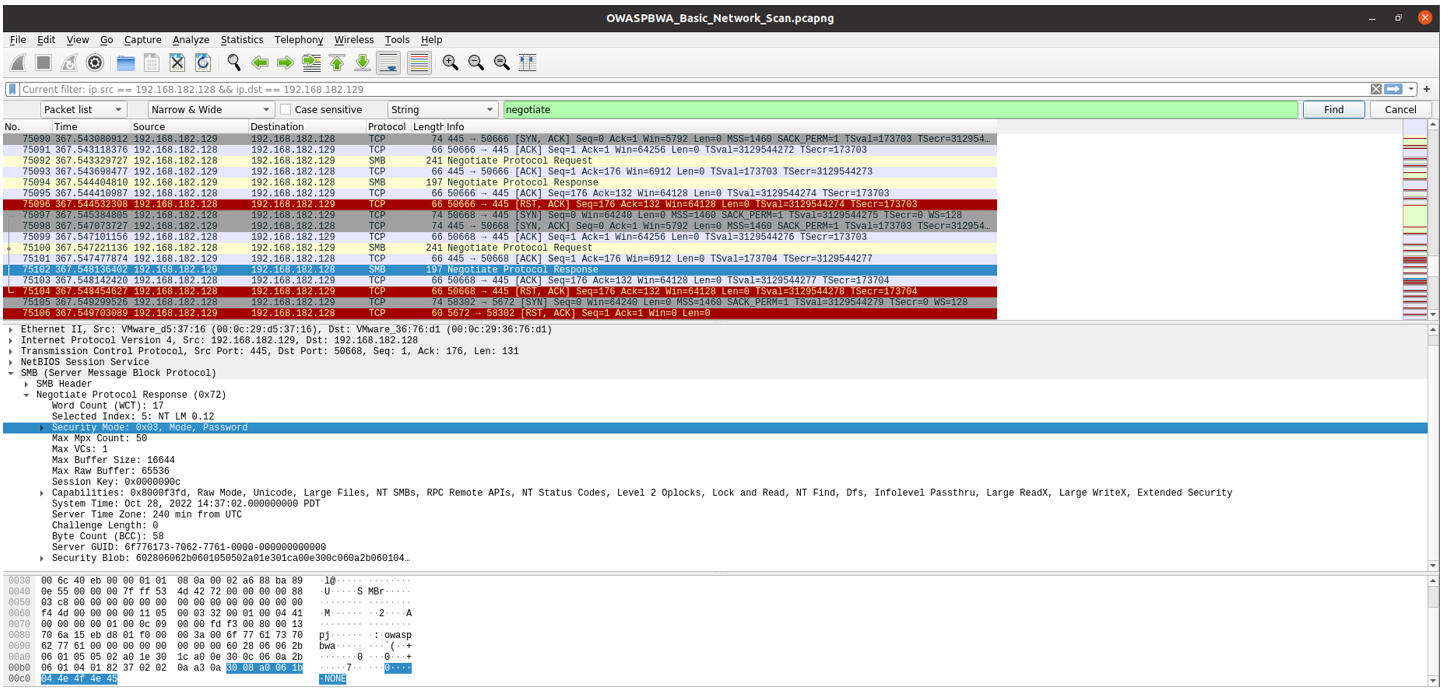
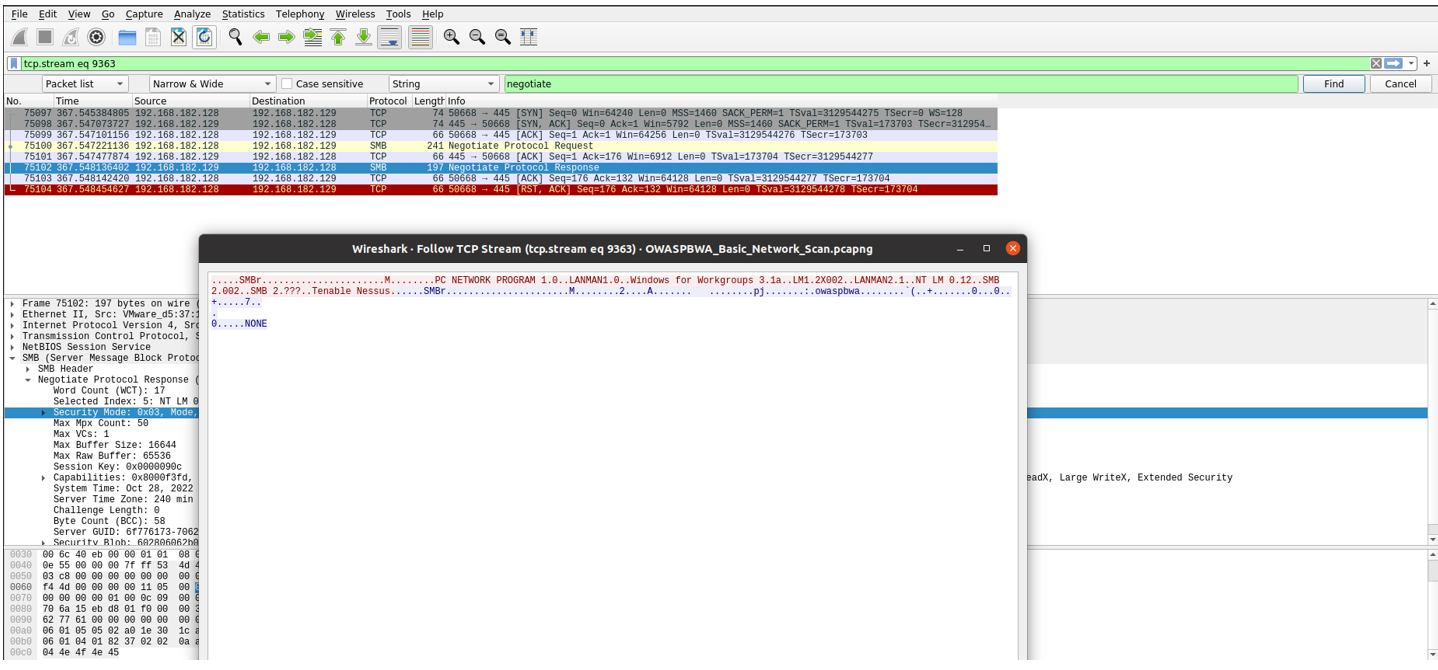
The Negotiate Response Packet shows that SMB Signing is not required.
Value of 3 represents SMB signing being disabled, 7 represents SMB signing enabled but not required, and 15 represents SMB signing enabled and required.
DVWA
OpenSSL < 0.9.8w ASN.1 asn1_d2i_read_bio Memory Corruption
Risk Factor
- High
CVSS v2.0 Base Score
- 7.5 (CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P)
CVSS v2.0 Temporal Score - 5.9 (CVSS2#E:POC/RL:OF/RC:C)
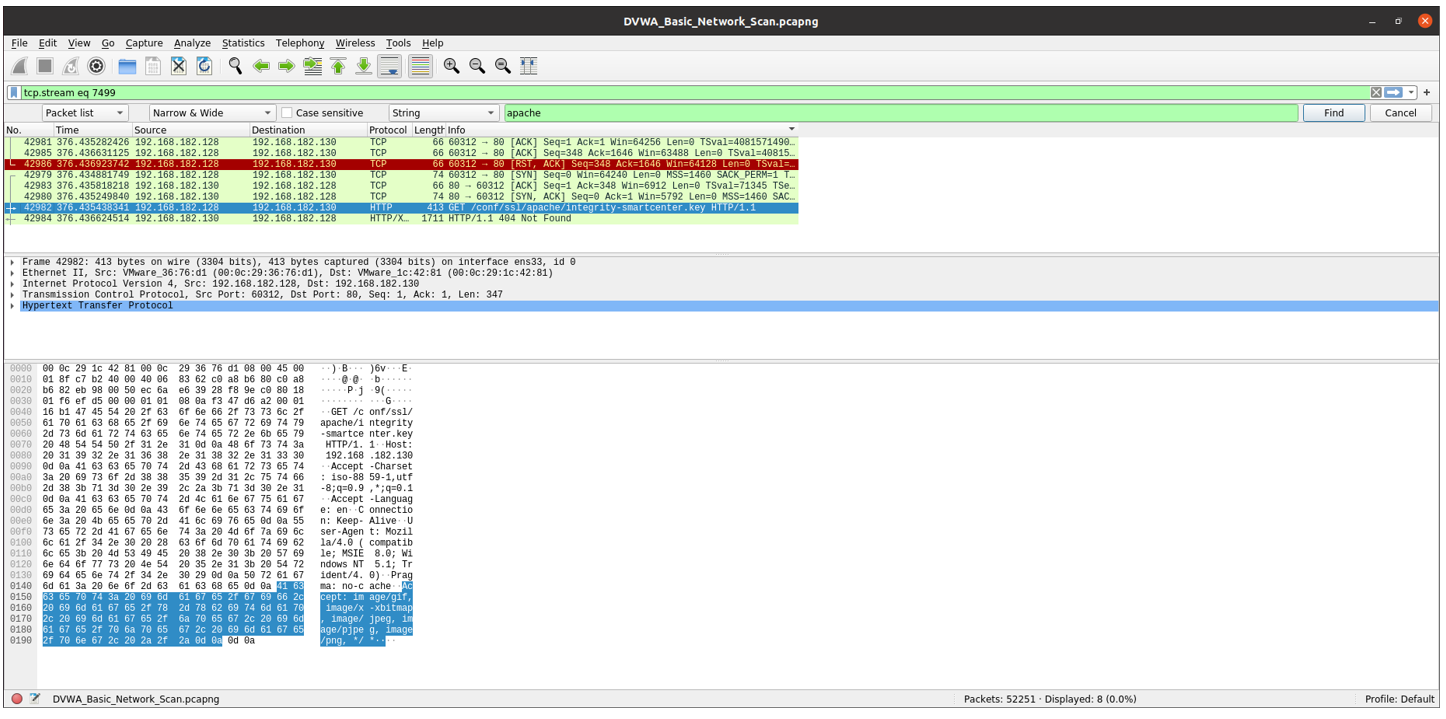
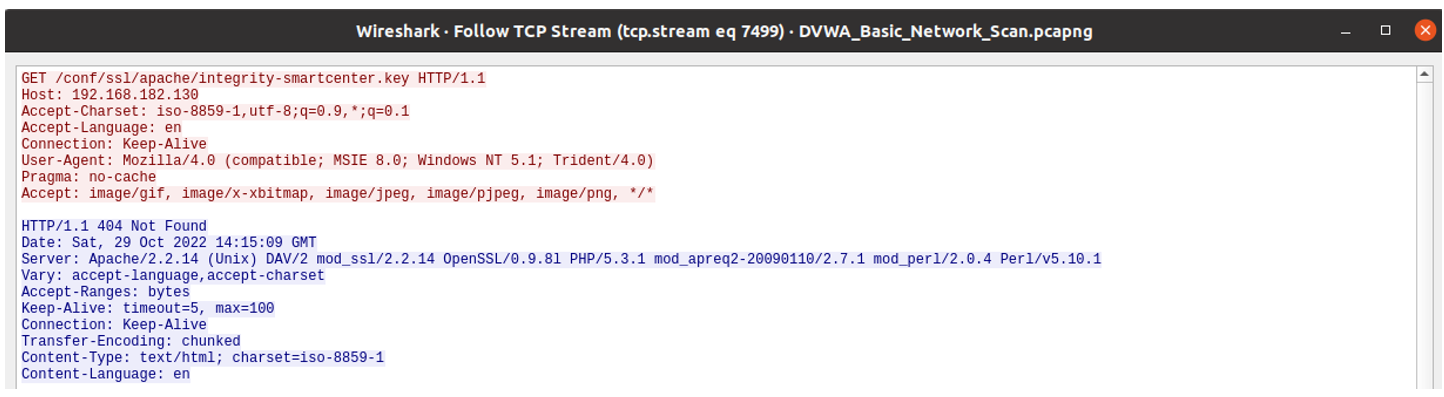
The banner header shows that it is vulnerable to OpenSSL vulnerability which leads to Memory corruption.
| Vulnerability | OWASP BWA | DVWA |
|---|---|---|
| SMB Signing not required | Yes | No |
| OpenSSL Memory Corruption | No | Yes |
3. For the two Web Application Tests Scans, select a vulnerability that was detected on one of the machines but doesn’t show on the report of the other machine. Identify the Wireshark packets related to the detection/probing of this vulnerability on both scans.
Web Application Scan
OWASP BWA
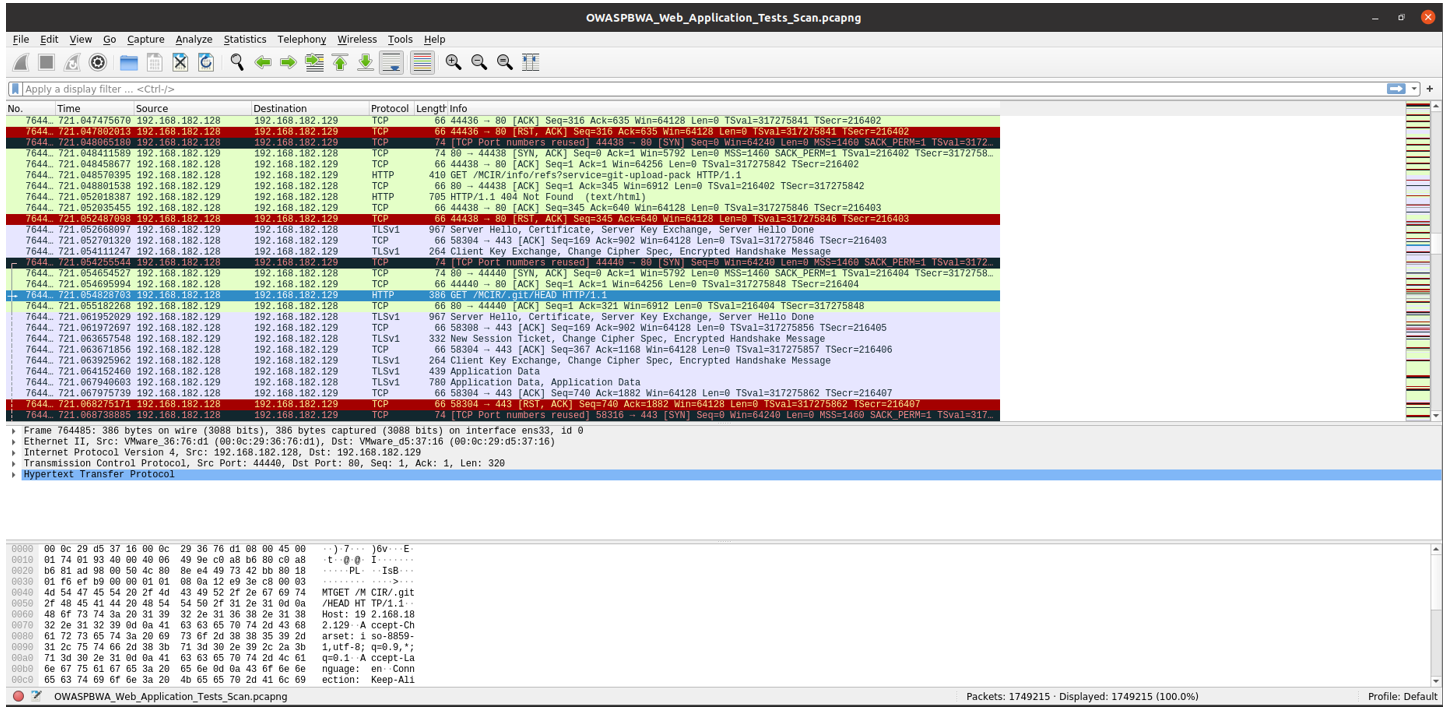
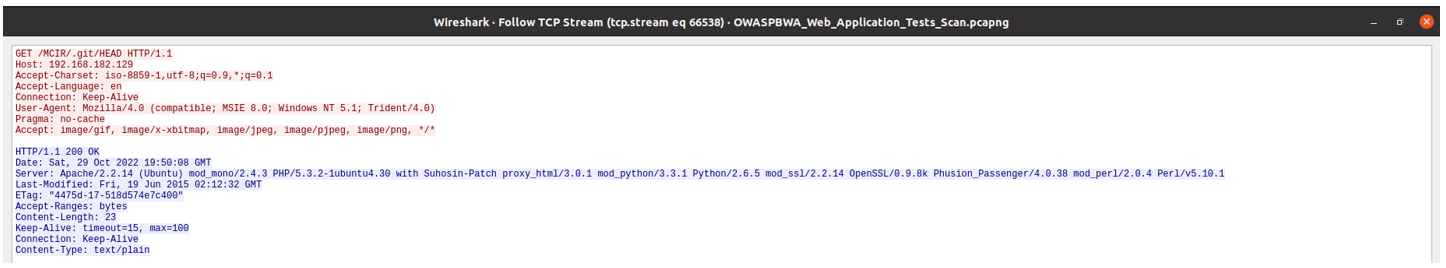
Git Repository Served by Web Server
Risk Factor
- Medium
CVSS v2.0 Base Score
- 5.0 (CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
DVWA
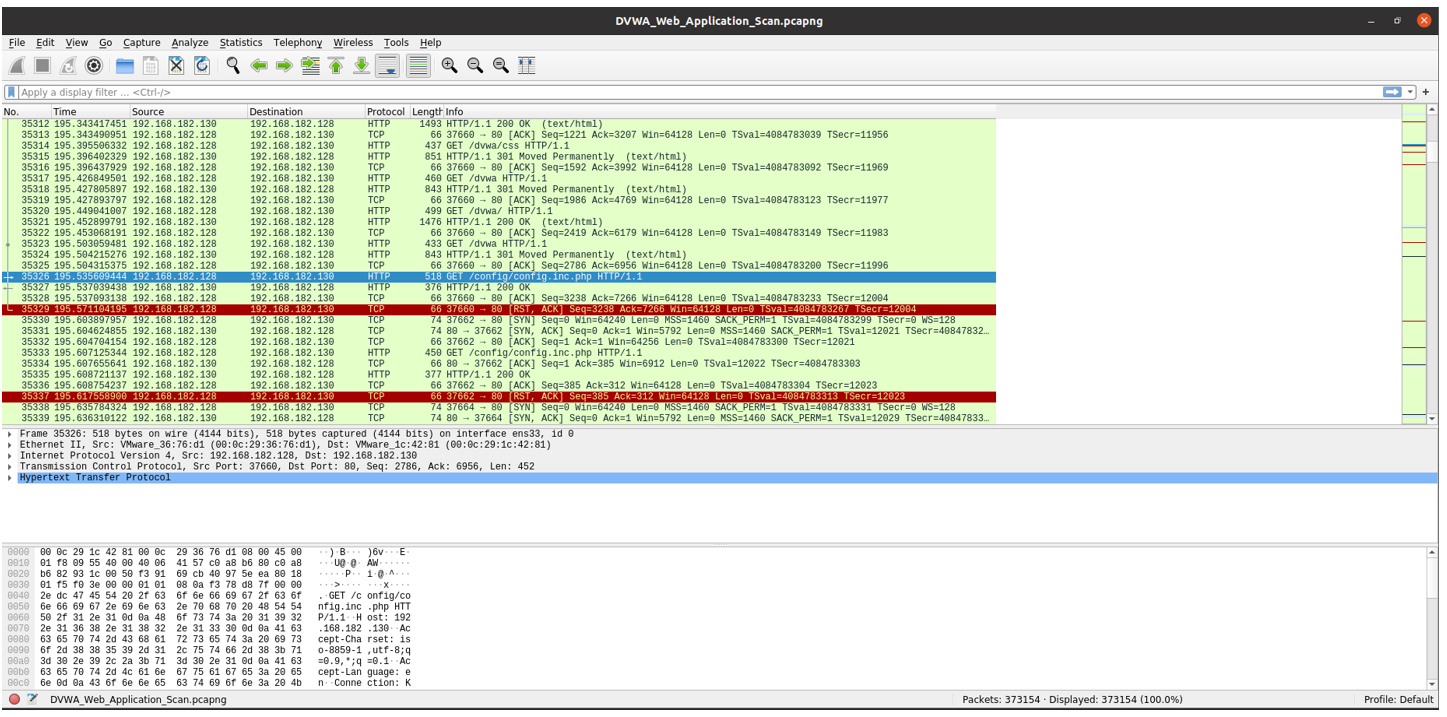
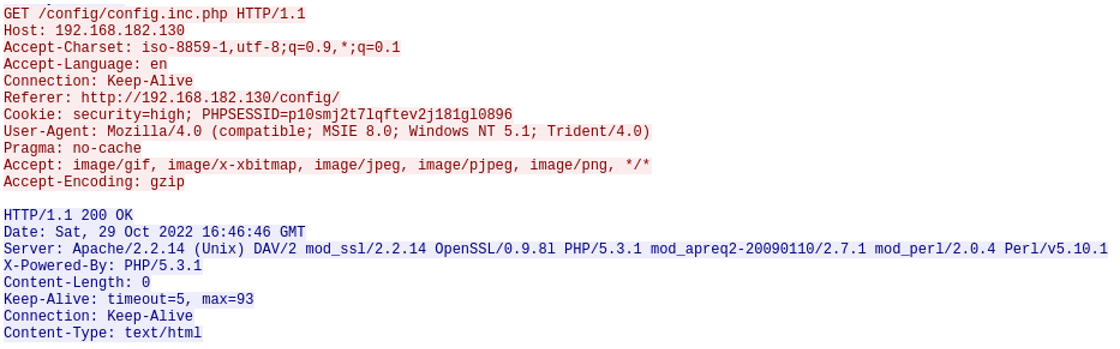
Risk Factor
Medium
CVSS v3.0 Base Score
5.3 (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/I:N/A:N)
CVSS v2.0 Base Score
5.0 (CVSS2#AV:N/AC:L/Au:N/C:N/I:N/A:N)