Forensic Analysis of Zeus Bot Attack
One of the most high-profile pieces of malware in the current threat landscape—studied here via TCPDUMP of infected traffic.
Name: Anurodh Acharya
One of the most high-profile pieces of malware in the current threat landscape—Zeus (aka Zbot)—has been used by botnet operators to steal banking credentials, participate in click-fraud schemes, and more. In this lab you’ll study Zeus’s post-infection behavior by analyzing a provided TCPDUMP of infected traffic. Try to find an answer to the following.
Diagram demonstrating the sequences involved in the attack
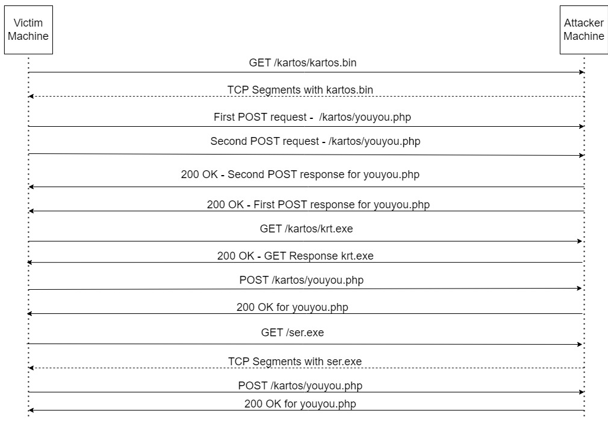
Observed Network Traffic
The bot initiates a GET request on /kartos/kartos.bin. Then it makes multiple POST requests on /kartos/youyou.php, likely exfiltrating data. Next it downloads krt.exe successfully. Finally, it requests /ser.exe—the response shows up only at the TCP level.
Questions & Answers
1. What is the IP address/country of the attacker/Zeus controllers and victim machine(s)?
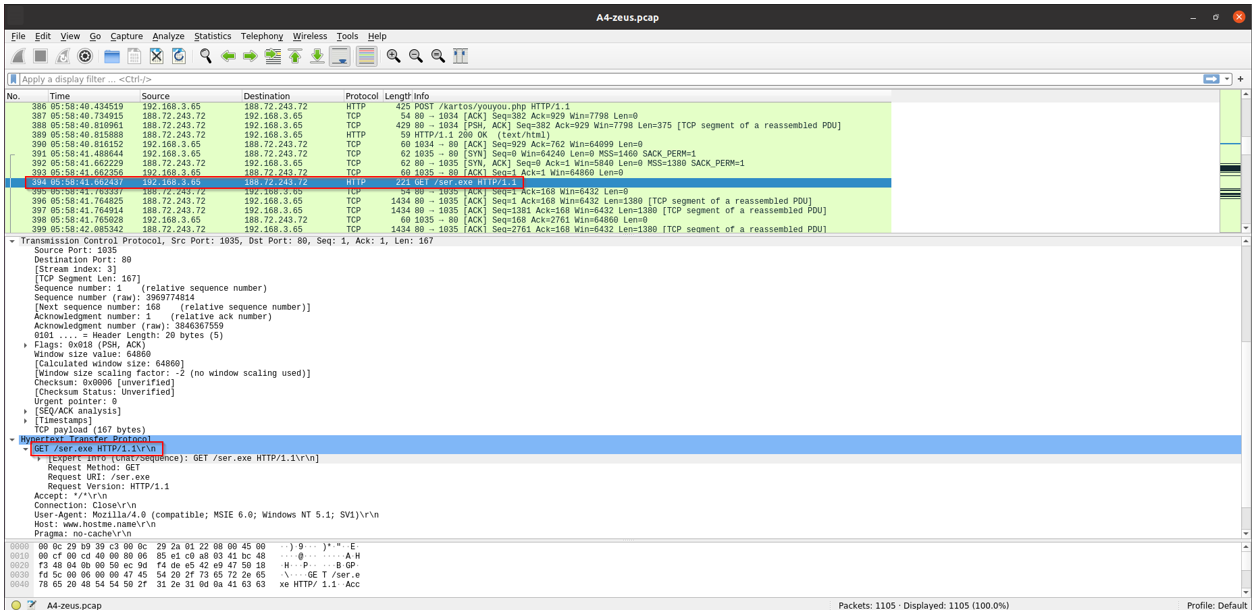
- Attacker IP: 188.72.243.72
- Victim IP: 192.168.3.65
- Attacker Country: Netherlands
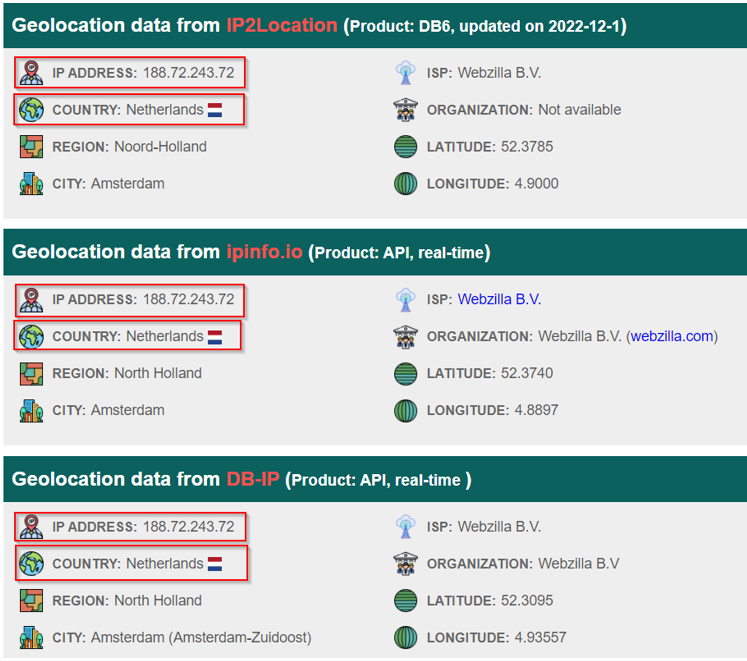
2. What is the operating system of the victim machine?
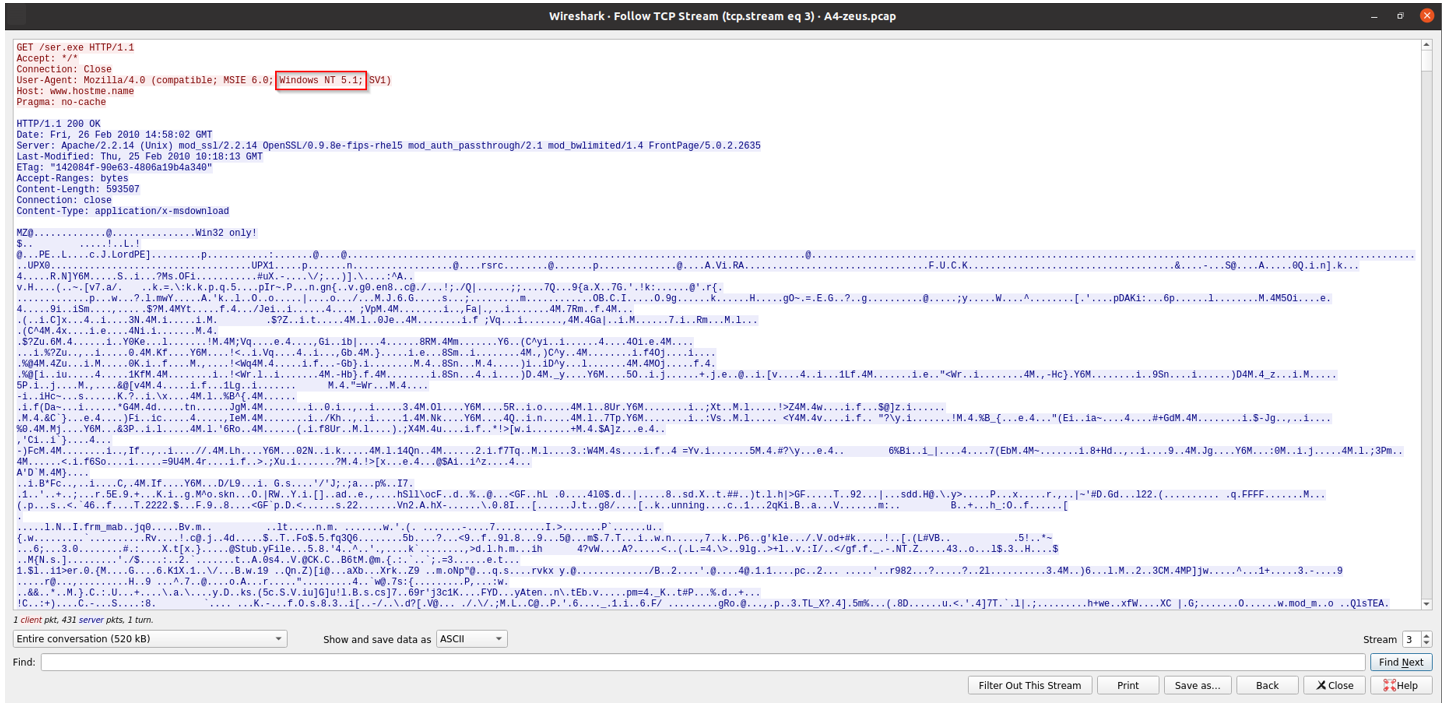
The TCP stream shows Windows NT 5.1, which corresponds to Windows XP.
3. Did the attacker succeed in downloading something to the victim’s machine?
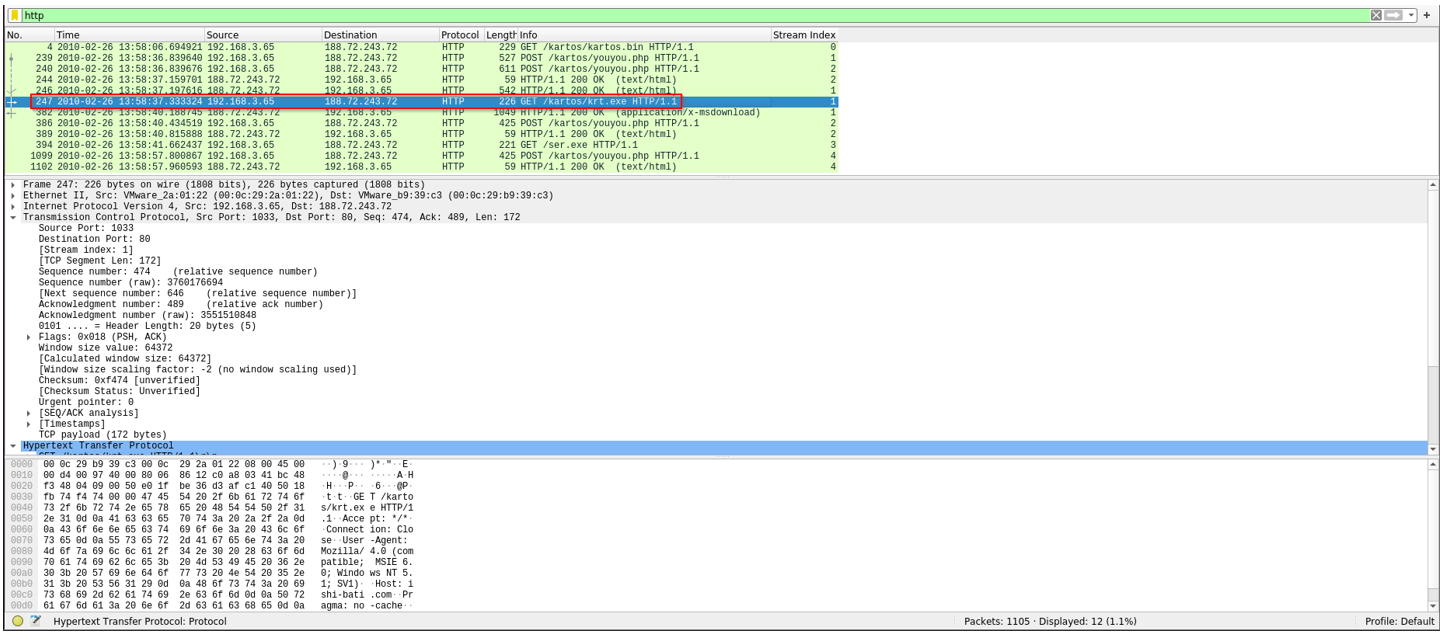
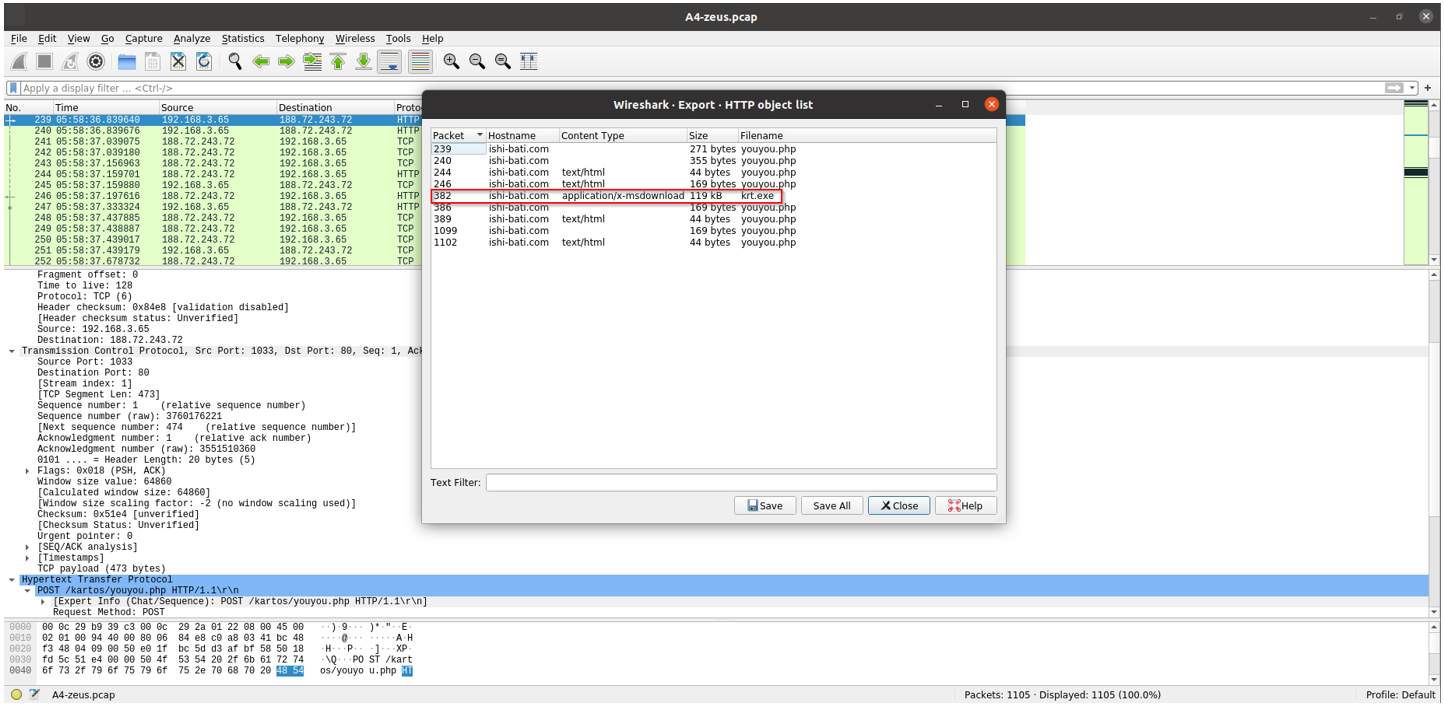
Yes — the attacker was able to download the file (krt.exe) onto the victim’s machine.
4. Was there a firewall on this network?
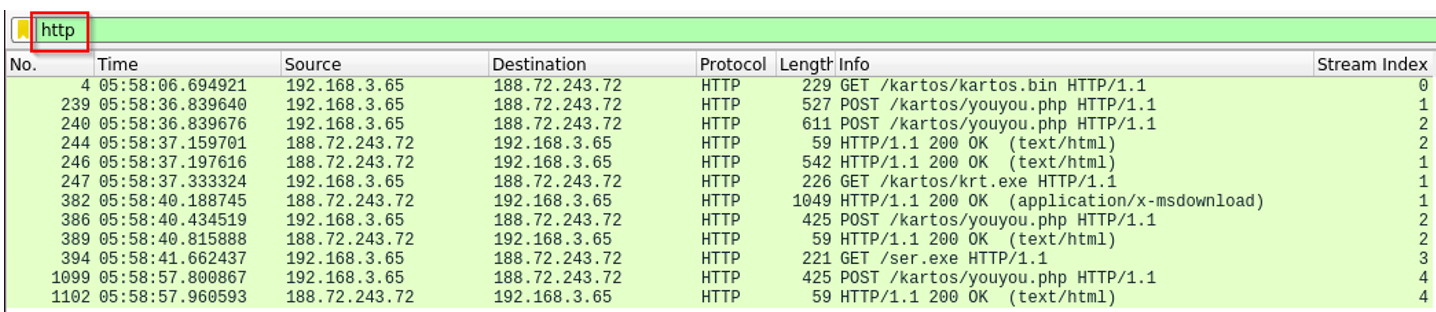
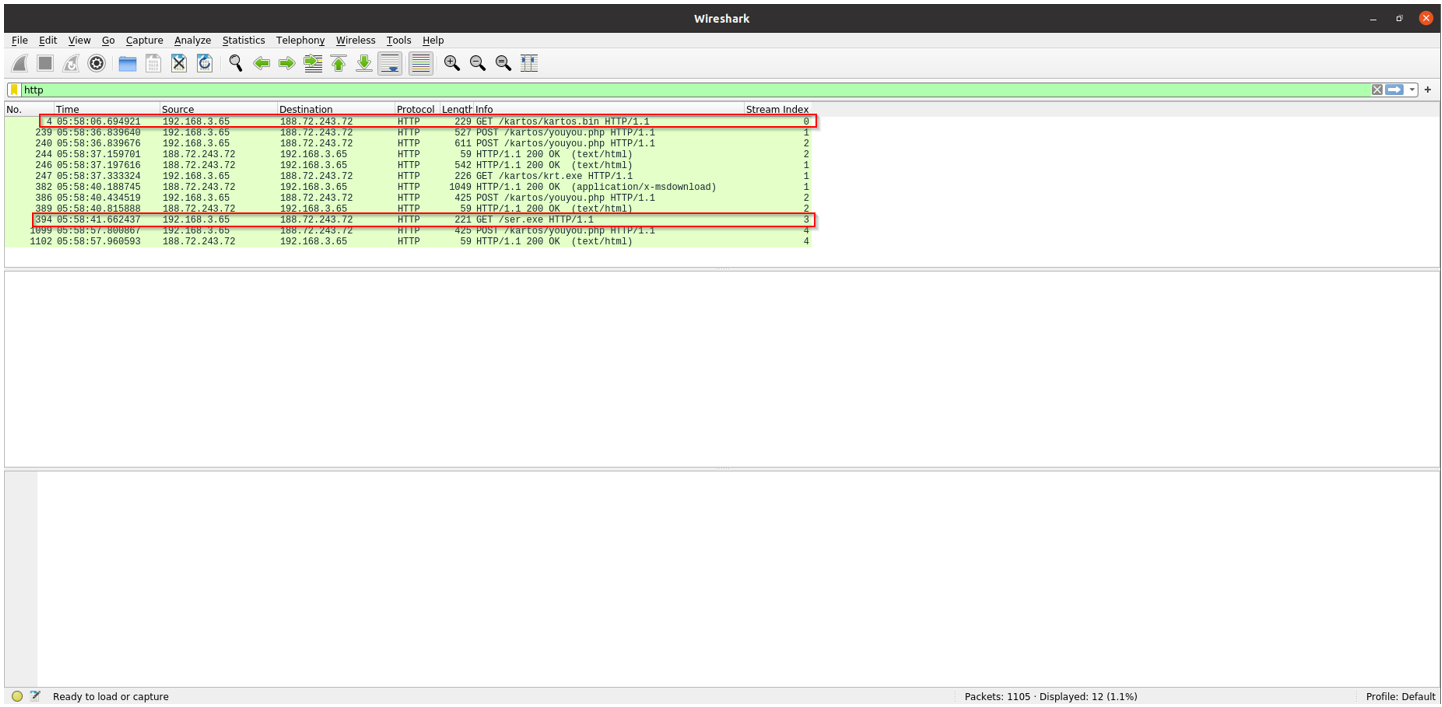
Two HTTP requests never received HTTP‐level responses; although TCP segments arrived, their missing HTTP replies suggest packet drops—possibly firewall rules blocking /kartos/kartos.bin or /ser.exe. Yet without a consistent block pattern, we can’t definitively confirm a firewall.
5. When did Zeus start to be active, and when did it stop?
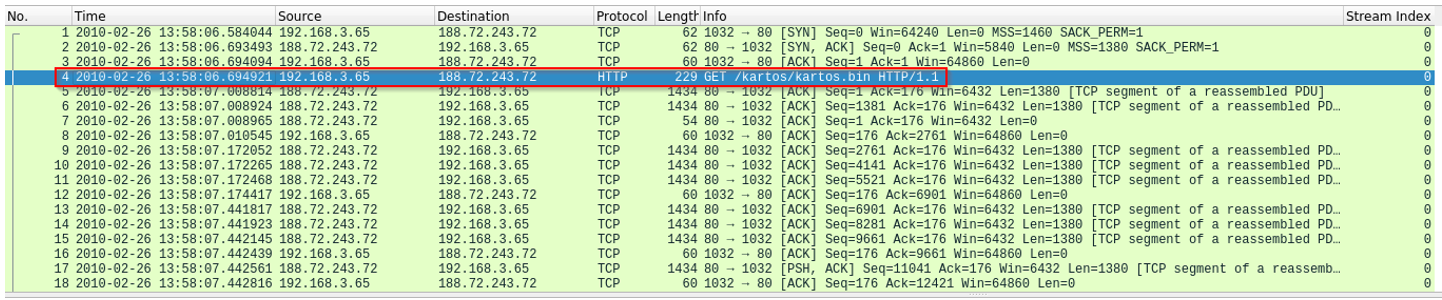
- Start: 2010-02-26 13:58:06.694921 UTC
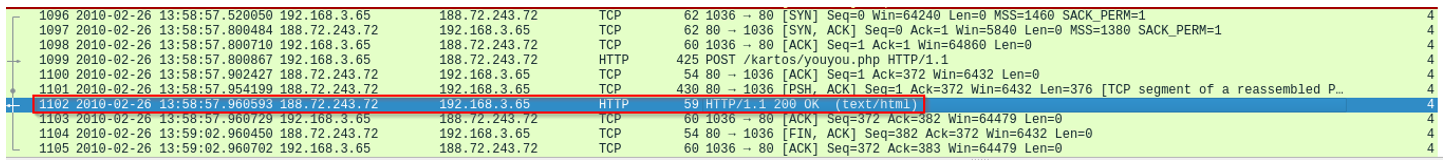
- End: 2010-02-26 13:58:57.960593 UTC
These correspond to the first GET for kartos.bin and the final TCP segments before the FIN handshake.
6. Could this trojan be detected by a simple IDS that looks at HTTP/TCP frequency?
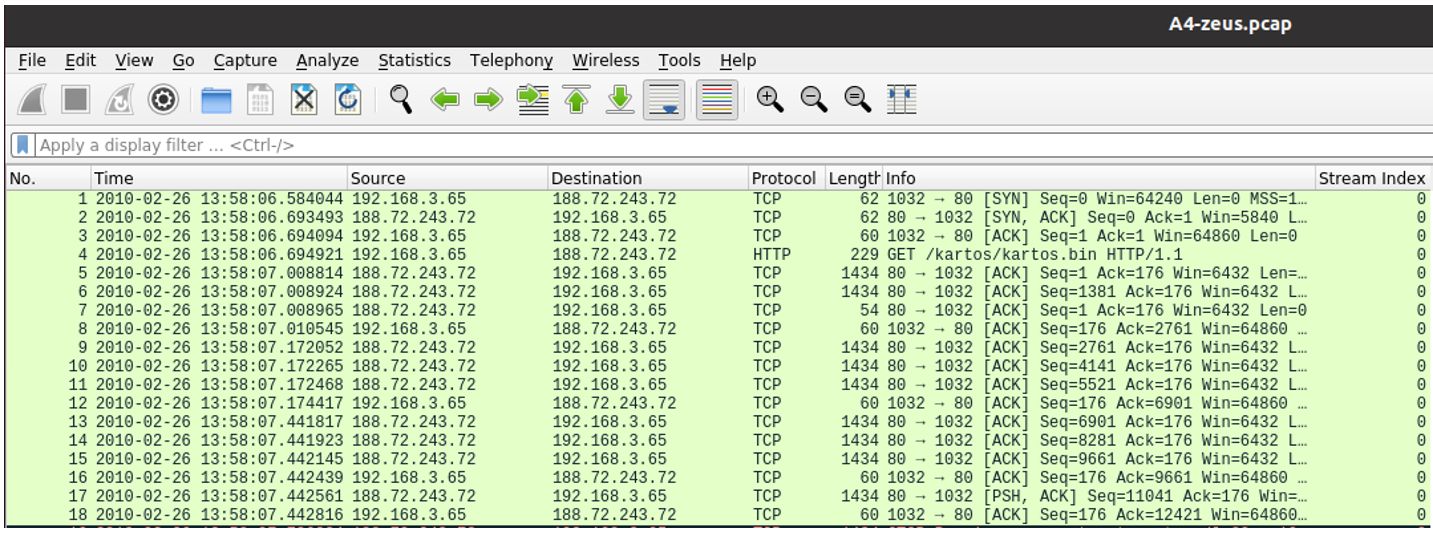
Only four TCP streams appear in total, so a naive IDS counting request rates would likely not flag this as malicious. A more advanced IDS—one that analyzes payload signatures or beaconing patterns—would be required for reliable detection.